
Threats don’t exist in the absence of system vulnerabilities. A threat is the probability of an operational hazard exploiting a specific system vulnerability which in turn affects business operations and revenue. System vulnerabilities are exposed either by chance or intentionally.
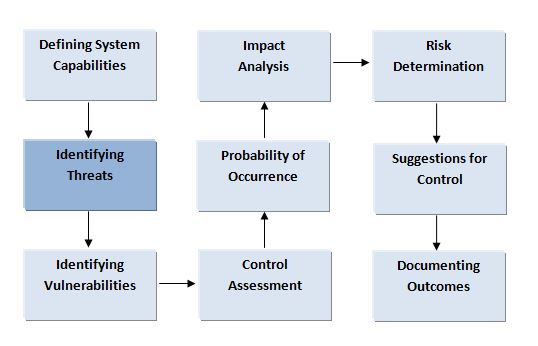
Identifying Threat Sources
Threat sources or hazards are specific operational scenarios that can trigger system vulnerabilities. These scenarios can be induced by
- Human Intervention
- Unauthorized Access
- Erroneous Data Entry
- Malicious Software
- Network Security Breaches
- Business Circumstances
- Power Outages
- Extreme Atmosphere Particulate Content
- Chemical and Oil Spills
- Environmental Conditions
- Floods
- Earthquakes
- Tornadoes
- Storms
- Fires
Threats Caused by Human Intervention
The manner in which the above mentioned threat sources and their respective outcomes erupt and progress over a period of time can vary from organization to organization depending on the nature, scale and complexity of operations. Further complications can also arise depending on the exposure of crucial players such as customers and interest groups to these hazards. Organizational culture is also a crucial factor that can influence efforts to mitigate threats.
Organizations can keep track of known threats through a variety of sources such as:
- In-house research and investigations
- Official sources such as a government agencies
- Professional experts and specialists in the private sector
- Online Resources
Data Breaches through Internal Employees
Data breaches are constantly rising every year. A substantial portion of these issues are created internal by employees and personnel. The growing concern over compromising highly confidential data has prompted many international official bodies to mandate security measures through regulatory norms such as General Data Protection Regulation (GDPR).
Company Personnel
The incidence of data breaches that result from internal causes has been steadily increasing. More than half of these incidents are unintentional, caused by a lack of attention to detail, carelessness or negligence. When highly classified information is freely sent and received across internal communication channels, the criticality of maintaining its confidentiality tends to get diluted, which in turns encourages unintentional misuse.
Educating Internal Employees
Regulations such as GDPR have now made it compulsory for enterprises to take responsibility for data breaches, even those caused by external factors such as vendors and contractors. This has made the abilities of internal employees to mitigate such threats all the more crucial.
Implications
The criticality of data depends on the department it corresponds to, be it finance, HR, development, marketing or admin. Employees must be made aware of the impact a data breach can have, both on department as well as organization deliverables. Through cross departmental training, personnel can be made aware of the value of data held by other departments.
Having a Plan for Data Protection
Organizations must make their commitment to data protection official through a rigorous company policy that comprehensively covers all aspects of safeguarding confidential corporate information, with a specific focus on employee training. This requires active involvement and support from upper management and leadership teams.
Prevention, response and restoration strategies must be developed and employees must be involved while implementing the resiliency framework.
Internal employees can be further empowered in this regard by:
- Building Awareness
- Transforming organizational culture
- Conducting training sessions and education programs
- Create Common forums of discussion for sharing different strategies perspectives and concerns and conflicting issues on data security
Network Security
To err is human and errors are bound to creep in while employee personnel handle data. However, corporations can use technology to add an additional layer of protection through access controls, adaptive redaction, data loss prevention software and so on. Sharing confidential data through emails that was overlooked by employees can be filtered and company interests can be safeguarded.
See for yourself how the application works
Witness our cloud based platform’s security capabilities in action
Play around with the software and explore its features
Compare and choose a solution that’s relevant to your organization
Consult our experts and decide on a pricing mechanism
Disasters
[carousel id=’1780′ items=’4′ items_desktop=’3′ margin_right=’5′ navigation=’false’] [item img_link=”https://www.stayinbusiness.com/wp-content/uploads/2016/02/Chemical-Spills-Discharges.jpg” href=”https://www.stayinbusiness.com/resource/disaster-recovery/chemical-spills-and-discharges/”][item img_link=”https://www.stayinbusiness.com/wp-content/uploads/2016/02/Riots-Public-Disturbances.jpg” href=”https://www.stayinbusiness.com/resource/disaster-recovery/riots-and-public-disturbances/”][item img_link=”https://www.stayinbusiness.com/wp-content/uploads/2016/02/Terrorism.jpg” href=”https://www.stayinbusiness.com/resource/disaster-recovery/terrorism/”] [item img_link=”https://www.stayinbusiness.com/wp-content/uploads/2016/02/worst-product-recall.jpg” href=”https://www.stayinbusiness.com/resource/disaster-recovery/product-recall/”] [/carousel]
