
More and more organizations are adopting cloud based solutions in a bid to increase business efficiency. While the technology comes with numerous advantages, strategies for accessing and storing data, as well as application distribution over the network are crucial.
Reasons for choosing cloud based solutions
Big Data
Public Cloud Infrastructure as a Service – Advantages include unlimited storage and computer power. Hardware costs are incurred by the cloud vendor.
Private Cloud Platform as a Service – Big Data technologies are an inbuilt feature in PaaS solutions.
Hybrid Cloud Software as a Solution – Ideally suited for facilitating detailed insights through business analytics.
Data Confidentiality
Data privacy can be ensured through approaches such as fragmentation and anonymization.
Security Breaches
- Most cloud solutions have inbuilt security features that are governed by stringent regulatory norms
- Cloud solutions facilitate protection against DDoS attacks, malware and other cyber threats
Advantages of Cloud Based Solutions
- Speed
- Scalable Options
- Operational Adaptability
- Competitive Pricing
- Improvements in efficiency and effectiveness
Potential Hurdles
- Application and System Availability
- Network Requirements
- Acquisition of relevant skills and expertise
- Budget Management
Statistical findings of Cloud based Solutions
- Dearth of skilled personnel – Enterprises are looking to bridge gaps in cloud based skills through training programs and hiring new staff with relevant certifications
- Data protection concerns – Information is shared with an external entity beyond the organization’s control which implies a certain amount of risk
- Budget management issues – IT teams tend to deploy many cloud instances that were only meant for short term use but stay active over extended periods of time, even while they are no longer in use, thereby implying additional costs
Operational Constraints
Data Protection and Confidentiality
Service provider takes responsibility for all security and confidentiality related concerns. But corporations still have to bear the risk of sharing company information with an external entity. The criticality of corporate security objectives can be enforced through explicit SLAs.
Cybercrimes
Data stored online is always vulnerable to security breaches and cyber attacks can’t be ruled out completely. These threats come in the form of:
- Bot Malware
- Brute Force Attacks
- Virtual Machines Vulnerabilities
Quality of Service
This is a major concern with most companies, especially those with mission critical workflows. Once again, organizations can ensure a minimum level of service quality through SLAs that specify:
- Bandwidth Requirements
- Threshold for Latency
- Application downtime tolerance and so on
Price
Cloud solutions that support applications that are heavy on data and need to work in real time are more expensive.
Integrating with existing infrastructure
Common Challenges Include:
- Supporting multiple flows across the corporate network as well as the cloud
- Lack of granular control and perceptibility over key performance metrics
- Provisioning open platforms that facilitate seamless integration
- Leveraging a “Bring your own device” Model
IT Governance
Enterprises need to choose a solution that maintains their assets in line with corporate policies, regulatory norms, industry standards and best practices.
Managing risk related to cloud based solutions
- Assigning Clearly defined roles and responsibilities
- Detailed SLAs that outline IT systems’ risk threshold
- Real time visibility, analysis, control and mitigation
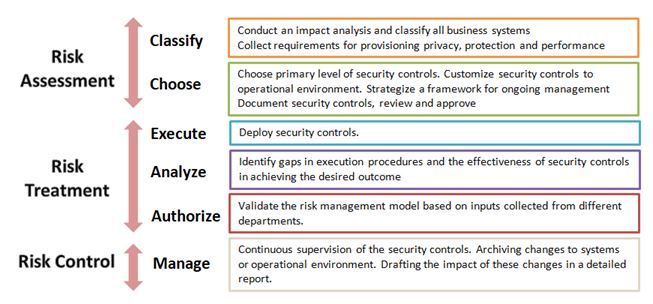
Risk Management Framework for Cloud Solutions
The Importance of Connectivity for Cloud Based Workflows
Efficient network management is more often than not the deciding factor while leveraging cloud based solutions.
Multiple Connections
Avoiding downtime and internet outages is crucial, especially when applications need to work in real time. With multiple network lines, enterprises can exploit the advantages of carrier neutral datacenters, such as:
- Cost Efficiency
- Growing Bandwidth Needs
- Diverse Connectivity Options to Choose From
Speed
Latency, jitter and inefficient bandwidth management affect the overall application delivery speed, as well as productivity.
Protection
Some organizations might prefer accessing their cloud servers through a VPN connection, or maybe even a direct line if all the other assets are located at the same data center. The right management tool with the right combination of functionalities needs to be chosen.
Networking Considerations for Different Cloud Solutions
Public Cloud
The internet is widely used here, although some vendors provide VPN tunnels as well. Public cloud solutions are marked by a constant conflict between security and performance concerns. Encrypted tunnels are not very common amongst public cloud vendors. So most of the time, company data is vulnerable to security breaches. However, encryption can significantly slow down application delivery.
One effective workaround to this problem is intelligently choosing the shortest route through the internet with the least number of transit hops across the network.
Private Clouds
Enterprises often use the networking solution implemented at their data centers to connect with their private clouds as well. This is usually an Internet VPN or even a VPN service from a service provider. Impact on performance is negligible in such scenarios.
Public Intra-Cloud
The end user cannot view the manner in which connectivity between public clouds is established. Network quality of service tends to vary across cloud resources as they are pooled together across different geographical regions. Some vendors allow customers to limit the physical range from which resources can be chosen. In such a scenario, companies must assess the difference in resource performance across the limited geographical range.
Private Intra-Cloud Solutions
Connectivity over here largely depends on the extent to which applications have a modular structure. In service oriented architecture (SOA), communication can be established between different components of the same application, or even between the application and the end user.
Large data centers connect over company provided network lines, so these connections must have the necessary capabilities to support application delivery, regardless of the application’s location in the private cloud.
See for yourself how the application works
Witness our cloud based platform’s security capabilities in action
Play around with the software and explore its features
Compare and choose a solution that’s relevant to your organization
Consult our experts and decide on a pricing mechanism
Disasters
[carousel id=’1780′ items=’4′ items_desktop=’3′ margin_right=’5′ navigation=’false’] [item img_link=”https://www.stayinbusiness.com/wp-content/uploads/2016/02/Chemical-Spills-Discharges.jpg” href=”https://www.stayinbusiness.com/resource/disaster-recovery/chemical-spills-and-discharges/”][item img_link=”https://www.stayinbusiness.com/wp-content/uploads/2016/02/Riots-Public-Disturbances.jpg” href=”https://www.stayinbusiness.com/resource/disaster-recovery/riots-and-public-disturbances/”][item img_link=”https://www.stayinbusiness.com/wp-content/uploads/2016/02/Terrorism.jpg” href=”https://www.stayinbusiness.com/resource/disaster-recovery/terrorism/”] [item img_link=”https://www.stayinbusiness.com/wp-content/uploads/2016/02/worst-product-recall.jpg” href=”https://www.stayinbusiness.com/resource/disaster-recovery/product-recall/”] [/carousel]
