
The benefits of implementing an SD-WAN solution far outweigh those of conventional router based WAN networks. This is true particularly in the case of modern day corporations with operations spread across the globe and a strong focus on cloud based application delivery.
Businesses no longer have to depend on legacy, private connections and can take advantage of broadband internet lines through an SD-WAN (Software-Defined WAN) solution. Application delivery and network speed can be enhanced while unnecessary capital expenditure can be curbed. However, it must be noted that these benefits can be reaped only by reaping an SD-WAN solution that is built on strong security.
This requires, at the very least, adequate infrastructural capabilities that can facilitate the required confidentiality and integrity while transmitting mission critical application data. But can enterprises afford to be satisfied with a functional level of data security?
SD-WAN solutions are a rapidly growing presence in today’s business arena. Organizations are eager to exploit their numerous benefits to make their business model more commercially viable without compromising on their security objectives.
One of the main advantages of an SD-WAN (Software-Defined WAN) solution is that companies can cut down on their internet expenses by subscribing to low cost connections. However, since these connections are public lines, IT teams must fortify their networks against intrusions, data breaches, information leaks and other such hazards. Here again, SD-WAN scores highly, with a range of benefits:
- Transmitting data to a central hub for security filtering is no longer necessary. Data can be sent out directly on to the internet from the batch location
- Bandwidth usage can be optimized
- Iaas and SaaS application performance are also improved
- Automation capabilities can be incorporated so that businesses can control staff requirements and reduce incidents due to manual errors
The result is a secure network strategy that goes beyond the needs of data protection and regulatory obligations.
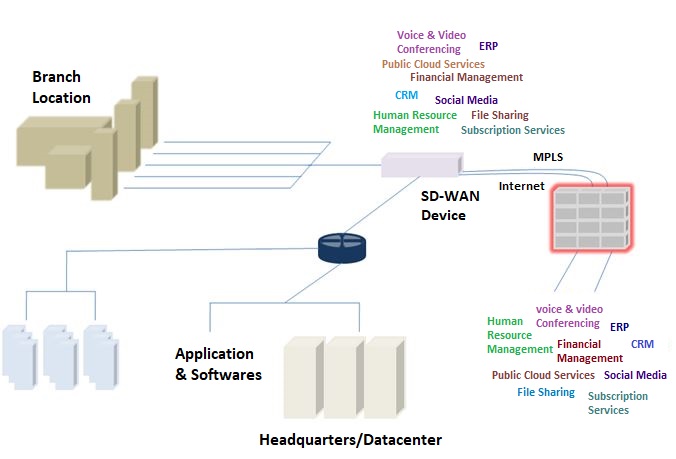
Figure 1 in the case of a functional SD-WAN solution, if application identity cannot be resolved the first packet, all the must be transmitted via the internet which can expose the branch location to a number of threats.
Alternately, all internet bound data can be routed to a firewall located at the main location for extensive security examination. If done inefficiency, this can be cumbersome process, increasing latency and impacting application performance.
SD-WAN’s Higher Purpose
The main focus of an SD-WAN solution is to efficiently establish communication channels between users who are spread across locations and geographical regions through the applications they access in the line of work. However, applications have evolved by leaps and bounds, especially with the advent of game changing technologies in recent times.
To cite an example, today, hosting applications in a corporate data center – be it a regional or a centralized location – is a thing of the past. Cloud based solutions and SaaS applications are creating new dimensions in the functional landscape of modern day business systems.
Real-time peer-to-peer communication is a prevalent feature in many present day applications which require better performance and a predominantly mesh based network structure.
Numerous systems are incorporating the Internet of Things (IoT) and Big Data apps in a bid to become more diverse and handle data volumes that keep rising exponentially every year. The corporate WAN must be able to take all these factors into consideration and leverage a solution that caters to application requirements on a case to case basis, based on parameters such as QoS, security, bandwidth and so on.
All these recent changes have influenced WAN solutions as well. Communication over conventional, private connections such as MPLS and routing methodologies such as backhauling are badly suited for cloud based applications, heavy data traffic and intense peer to peer information exchange.
Firstly, such services and architectures are expensive. Network performance is deeply impacted, especially in the case of data transmissions directed towards the internet or cloud. Secondly, modifying configurations and settings even at a cursory level can be slow and cumbersome which can severely compromise IT responsiveness and business agility.
SD-WAN, on the other hand, can bring together different types of networks, including broadband connections, and facilitate uninterrupted access to applications for end users. But IT teams must be ready to proactively prepare against the resulting security breaches.
State of the art SD-WAN solutions are heavily application centric while using and managing WAN capabilities, including configuration settings and security measures. The benefits, in concrete terms, are:
At branch offices, application data that is sent out to and received from the internet first passes through the organization’s primary office for security inspection. This constant back and forth of data between the branch and headquarters via WAN connections slow down network speeds. The enhanced capabilities of SD-WAN solutions can bypass this requirement. Data for specific applications can be directly transmitted to and received from the internet without running the risk of security breaches.
- Qualitative and Quantitative improvements in application output
- High Availability
- Financially viable total cost of ownership of WAN
- High Speed Networks
- Business Agility
- Improved Protection
Data Security – An Integral Feature of any SD-WAN Deployment
SD-WAN can optimize network efficiency at a competitive price by using low cost internet connections. However, since these connections are public, networks must be doubly fortified on security measures, especially in the case of SD-WAN devices that are deployed inline which have to directly confront cyber attacks. From a security perspective, SD-WAN devices in an inline deployment work a lot harder than conventional WAN accelerators located on the fringes of a network.
This is particularly true in the case of data that is transmitted directly onto the internet without first passing through the headquarters for security checks. Outbound destinations need to be filtered. Suspicious and undesired incoming data must be blocked. Only solicited packets must be transmitted or received after being thoroughly scanned for malicious content.
The SD-WAN solution needs to intelligently sift through the different types of internet traffic for viruses, trojans, DDoS attacks and other possible security breaches. For instance, a security protocol for web based traffic can be outlined in the following manner:
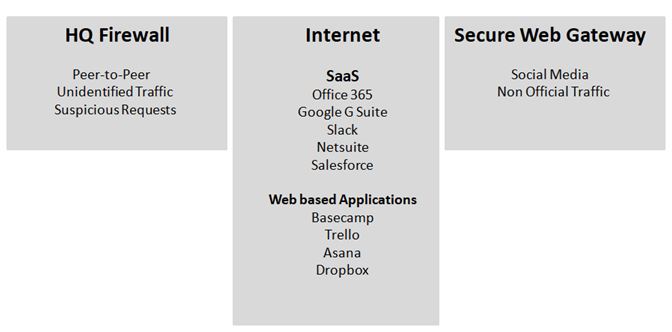
Such a strategy requires a granular level of control over the traffic routes. The identity of applications should be resolved after processing the first packet. This is crucial because once the session has been initiated; rerouting it to an alternate location would interrupt the traffic flow and cause an application disruption. Additionally, address tables must be updated using automation tools and the implementation must be carried out every day. This is because SaaS applications use IP address ranges that are constantly changing.
Other security related considerations while deploying an SD-WAN strategy:
- When applications with different cyber protection requirements use the same internet connection
- While reducing deployment time frames and increasing management efficiency, for instance, automating
- SD-WAN Provisioning
- Security Policy Enforcement
- Management Plan Security
- Standardized and uniform implementation of security measures pertaining to specific applications, irrespective of location or mode of access
See for yourself how the application works
Witness our cloud based platform’s security capabilities in action
Play around with the software and explore its features
Compare and choose a solution that’s relevant to your organization
Consult our experts and decide on a pricing mechanism
Disasters
[carousel id=’1780′ items=’4′ items_desktop=’3′ margin_right=’5′ navigation=’false’] [item img_link=”https://www.stayinbusiness.com/wp-content/uploads/2016/02/Chemical-Spills-Discharges.jpg” href=”https://www.stayinbusiness.com/resource/disaster-recovery/chemical-spills-and-discharges/”][item img_link=”https://www.stayinbusiness.com/wp-content/uploads/2016/02/Riots-Public-Disturbances.jpg” href=”https://www.stayinbusiness.com/resource/disaster-recovery/riots-and-public-disturbances/”][item img_link=”https://www.stayinbusiness.com/wp-content/uploads/2016/02/Terrorism.jpg” href=”https://www.stayinbusiness.com/resource/disaster-recovery/terrorism/”] [item img_link=”https://www.stayinbusiness.com/wp-content/uploads/2016/02/worst-product-recall.jpg” href=”https://www.stayinbusiness.com/resource/disaster-recovery/product-recall/”] [/carousel]
